Table of Contents
How VPN Works Step By Step
How VPN Works Step By Step: In an age dominated by digital connectivity, concerns about online privacy and security have become more pronounced than ever. Virtual Private Networks (VPNs) have emerged as essential tools for safeguarding online activities. This article aims to demystify the workings of VPNs, providing a detailed step-by-step understanding of how these networks operate to ensure user privacy, security, and unrestricted access to the internet.
- Understanding the Need for VPNs: As users traverse the internet, their data is susceptible to interception by malicious actors, internet service providers (ISPs), or even government agencies. VPNs address this vulnerability by creating a secure and encrypted connection between the user’s device and a server, ensuring that sensitive information remains private and protected.
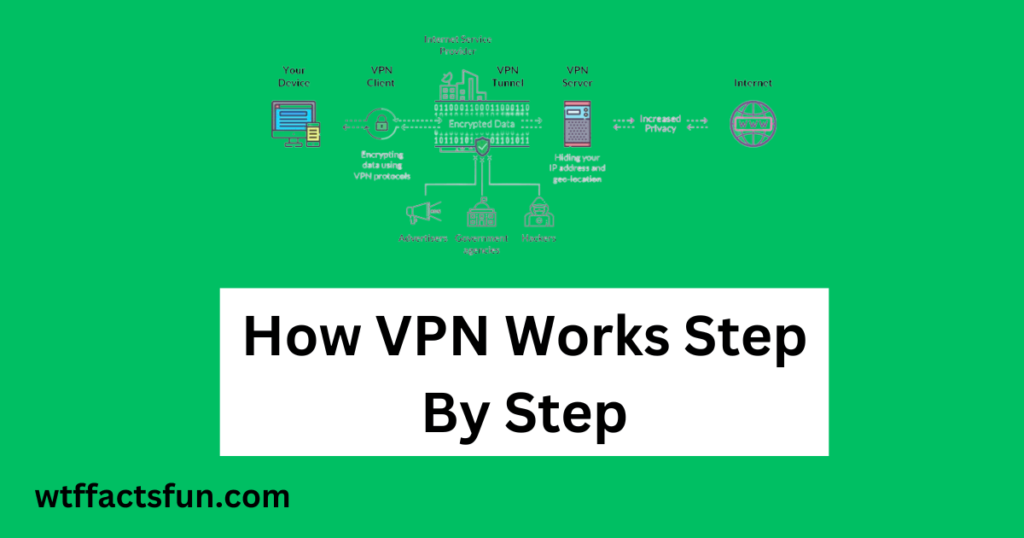
- Step 1: Connection Initiation: The VPN process begins with the user initiating a connection to their chosen VPN service. This can be achieved through dedicated VPN software or built-in features on certain devices and operating systems.
- Step 2: Encryption of Data: Once the connection is established, the VPN encrypts the user’s data. Encryption is a crucial aspect of VPN functionality, as it transforms the data into an unreadable format, making it nearly impossible for unauthorized entities to decipher and access sensitive information.
- Step 3: Tunneling Protocols: VPNs utilize tunneling protocols to encapsulate the encrypted data for secure transmission. Common protocols include OpenVPN, L2TP/IPsec, and IKEv2/IPsec. These protocols define how data packets are formatted and transmitted between the user’s device and the VPN server.
- Step 4: Secure Transmission to VPN Server: Encrypted and encapsulated, the user’s data is now transmitted through a secure tunnel to the VPN server. This process shields the data from potential eavesdropping, ensuring that even if intercepted, it remains indecipherable to unauthorized parties.
- Step 5: IP Address Concealment: VPNs provide users with the ability to mask their real IP addresses. Instead of revealing the user’s actual location and identity, the VPN server assigns a temporary IP address. This not only enhances privacy but also allows users to access geo-restricted content by appearing as though they are connecting from a different location.
- Step 6: Data Decryption at VPN Server: Upon reaching the VPN server, the encrypted data is decrypted. The server acts as an intermediary, decrypting the information and sending it to the intended destination—whether it’s a website, an online service, or another user—on behalf of the original user.
- Step 7: Destination Server Interaction: The destination server, be it a website or an online service, receives the data as if it originated from the VPN server. This ensures that the user’s real IP address and identity remain concealed, fostering anonymity and protecting against potential tracking or monitoring.
- Step 8: Return Transmission via Encrypted Tunnel: Any data transmitted back from the destination server follows the reverse path through the VPN server. The data is once again encrypted, ensuring that it remains secure during transit back to the user’s device.
- Step 9: User Device Decryption: The user’s device receives the encrypted data and decrypts it using the established encryption keys. This final step ensures that the user can access the information or services in their original, readable form.
Conclusion:
In a world where digital privacy and security are paramount, understanding how VPNs work step by step becomes essential. From the initiation of a secure connection to the encryption, tunneling, and IP address masking processes, VPNs offer a robust solution for users seeking to navigate the digital realm with confidence. By grasping the intricacies of VPN functionality, individuals can make informed choices about their online privacy and security, leveraging these tools to maintain control over their digital footprint and protect their sensitive information from potential threats.
Read also: